
In this digital era, security breaches occur on the websites frequently leading to hack user information. As the developers have to be updated and tackled with the issues on security malware, here are some important security menaces in PHP and HTML5.
Security Threats in PHP
SQL Injection:
In this threat, vicious user enters SQL in form fields that affects the execution of the SQL statements.
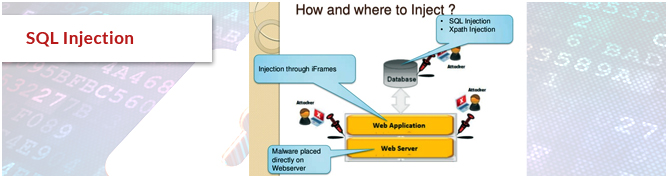
Prevention: Filtering the input data, manually checking the data.

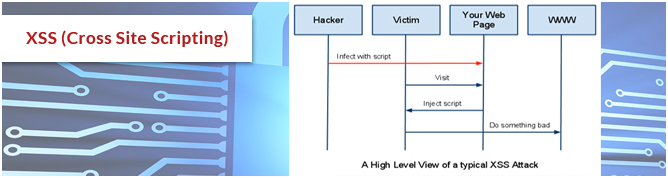
XSS (Cross Site Scripting)
XSS is an exploitation of user’s identity.XSS enables the user to insert data includes client side scripting that leads annoying pop ups and corrupted pages. Without filtering the data entered into the website, this script will be executed.
Prevention: Filtering the output using htmlentities() in PHP
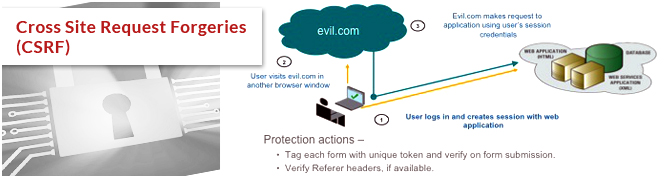
Cross Site Request Forgeries (CSRF)
CSRF is threat of exploiting the site’s trust in the client software. It is a threat of performing unwanted things in the website by authenticated user. Requesting a page that look like it was initiated by trusted users.
Prevention: Regenerating ID’s and user SSL for every session, generating one time token.
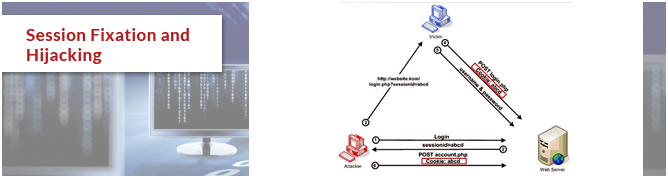
Session Fixation and Hijacking
In PHP, session works on PHPSESSID accepts through a cookie or through URL. Phishing attack is possible through session fixation. It is an attack of hijacking a user session. If the session ID is stored in the cookies it can be stole them through XSS and Java Script and if it is stored in URL it can be incurred from proxy server.
Prevention: Regenerating ID’s frequently.
Code Injection
Also called as Remote File Inclusion (RFI), allows an attacker to insert unwanted code into the web applications. Code injection occurs with the inclusion of external resources called Remote File Inclusion (RFI). The basal causes for code injection are input validation failures, non trusted input by the user and fail to secure source code of the PHP. It occurs when arbitrary code executes accidently.
Prevention: Filtering user input, Disabling allow_url,fopen and allow_url_include settings in php.ini
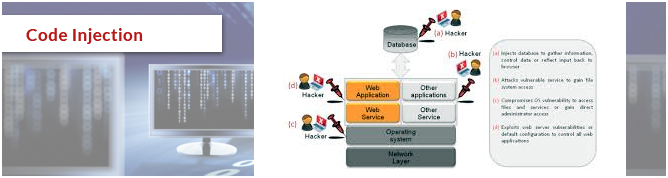
Security Threat in HTML5
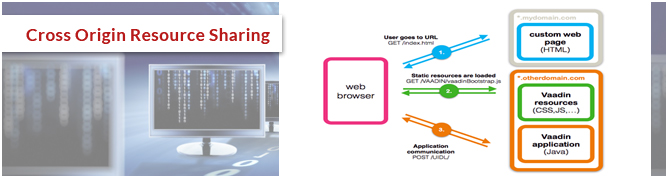
Cross Origin Resource Sharing
HTML5 applications make use of resources provided by the company and other providers. The main issue in this threat is allowing the resources to be used and shared among the external unauthorized users. By developing applications using HTML5, developers have to ensure that no sensitive data leaked to the external sources. Accessing the secured data should be restricted to the unauthenticated users.
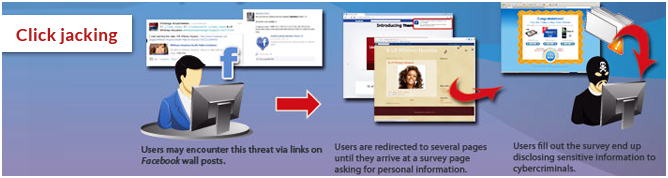
Click jacking
Tap jacking also known as “UI redress attack”, vicious technique inducing web user to click unwanted link which reveals the confidential information to the hacker. This attack has been prevented by configuring the application server to distribute the server only if it is in the upper most view.
Although with the advanced designing techniques most harmful attacks and vulnerabilities can be avoided, it is more important for the developers to tackle with the tardiest security issues and to make hackers to find more blot out exploits.

